
IT Support For Your Long-Term Care Facility
Veltec Networks provides IT support and IT services for long term healthcare facilities in the San Francisco Bay Area.

5 Cybersecurity Threats IoT Devices Pose To Businesses
It is estimated that by 2023, CIOs will be in charge of three times as many endpoints as they were in 2018. Why?

PointClickCare Support For Long-Term Care Facilities
Veltec Networks provides support and services for long-term care facilities that are running PointClickCare. Call for help today.

The Importance Of Backing Up Your SaaS Data
Consider the findings of the 2020 IT Operations Survey Report, in which 60% of the respondents claimed that their data is private and secure in the[...]

Veltec Networks Provides Comprehensive IT Services For SPT Microtechnologies USA, Inc.
Over the course of these past three years, Veltec Networks has shown the SPT Microtechnologies staff how much simpler and more effective their IT can[...]

Veltec Networks Helped This Hardware Manufacturer Set Up And Manage Their Linux-Based Data Center
As popular as Windows and iOS operating systems are, they’re not always the best choice. Businesses operating in highly specialized industries often have technical requirements[...]

How Much Does The Average Cyber Attack On An MSP Cost?
Managed service providers (MSPs) are likely well aware of the changing cybersecurity landscape and sophistication of cybercriminals.

Real Insights Into The Threats From Ransomware & Cybercrime
Veltec Networks is San Jose's leading authority in helping local businesses with ransomware and cybercrime.

What is Kari’s Law?
Kari's Law amended the Communications Act of 1934, and it requires multi-line telephone systems (MLTS) to enable users to directly dial 911 without having to[...]

President Biden’s Cybersecurity Executive Order
President Joe Biden signed an Executive Order on May 12, 2021, in a bid to strengthen cybersecurity in the United States and secure federal agency[...]

Insider Threats: Spotting Common Indicators and Warning Signs
Data protection regulations require your business to assess all possible threats to the sensitive data your business stores or manages. While most businesses tend to[...]
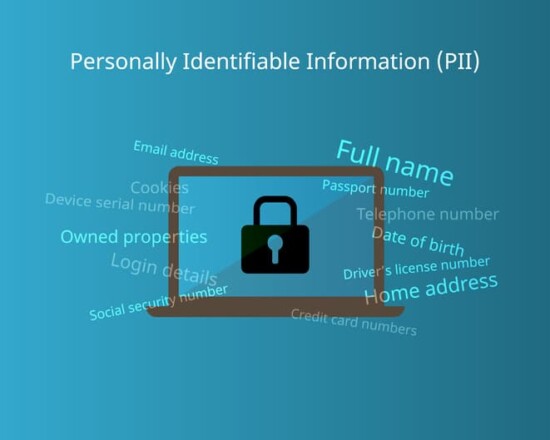
Potential Risks That Insider Threats Pose to PII
Personally Identifiable Information (PII) refers to any information maintained by an agency that can be used to identify or trace a specific individual.


